Hardware Security Module Market
Hardware Security Module Market Size, Scope, Growth, Trends and By Segmentation Types, Applications, Regional Analysis and Industry Forecast (2025-2033)
Report ID : RI_702537 | Last Updated : July 31, 2025 |
Format : ![]()
![]()
![]()
![]()
Hardware Security Module Market Size
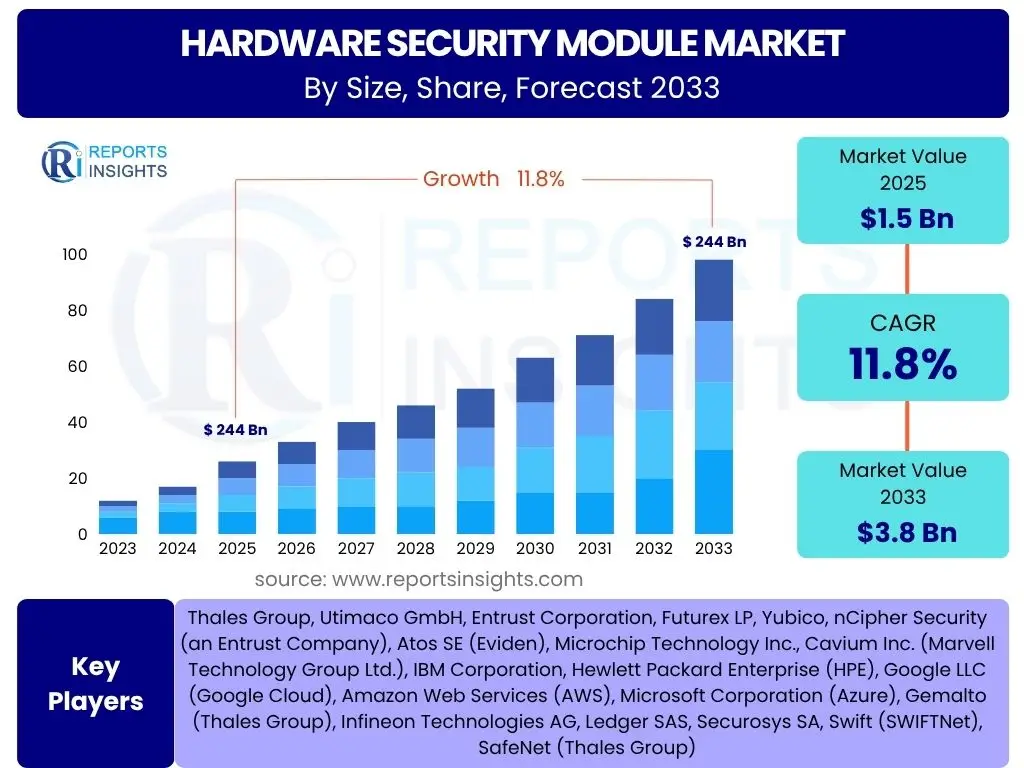
According to Reports Insights Consulting Pvt Ltd, The Hardware Security Module Market is projected to grow at a Compound Annual Growth Rate (CAGR) of 11.8% between 2025 and 2033. The market is estimated at USD 1.5 billion in 2025 and is projected to reach USD 3.8 billion by the end of the forecast period in 2033. This growth trajectory is significantly influenced by the escalating global demand for robust data security solutions across various industries, coupled with stringent regulatory compliance requirements mandating advanced cryptographic protection.
The expansion of digital transformation initiatives and the proliferation of cloud-based services are driving the adoption of Hardware Security Modules (HSMs). Enterprises are increasingly investing in HSMs to safeguard critical cryptographic keys, which are fundamental to securing sensitive data, transactions, and identities. This market expansion reflects a proactive response to the rising sophistication and frequency of cyberattacks, underscoring the indispensable role of hardware-based security in modern IT infrastructures.
Key Hardware Security Module Market Trends & Insights
Common inquiries about Hardware Security Module (HSM) market trends often center on their integration with evolving IT environments, the impact of new cryptographic standards, and the shift towards cloud-based solutions. Users are keenly interested in how HSMs are adapting to distributed architectures, the role of quantum-safe cryptography, and the increasing demand for high-assurance security in sectors like finance and healthcare. There's a notable focus on the balance between on-premise control and the scalability benefits of cloud-based HSMs, as well as their utility in emerging technologies like blockchain and IoT.
The market is witnessing a significant drive towards cloud-based and as-a-service HSM offerings, reflecting a broader industry shift towards flexible and scalable infrastructure. This trend is complemented by the growing emphasis on advanced cryptographic agility, enabling organizations to adapt to new algorithms and post-quantum cryptographic standards seamlessly. Additionally, the integration of HSMs with DevOps practices and automation tools is becoming crucial, facilitating more efficient and secure software development lifecycles.
- Increased adoption of cloud-based HSMs (HSM-as-a-Service) for enhanced scalability and reduced operational overhead.
- Growing demand for HSMs supporting post-quantum cryptography (PQC) readiness as quantum computing threats emerge.
- Rising integration of HSMs with blockchain and distributed ledger technologies (DLT) for secure digital asset management.
- Enhanced focus on cryptographic agility and multi-algorithm support within HSMs to address evolving security standards.
- Proliferation of IoT devices driving demand for HSMs for secure device authentication and data integrity at the edge.
- Convergence of HSM functionalities with identity and access management (IAM) solutions for stronger authentication protocols.
AI Impact Analysis on Hardware Security Module
User questions regarding the impact of AI on Hardware Security Modules (HSMs) frequently revolve around how AI can enhance HSM capabilities, whether AI poses new threats that HSMs must defend against, and the potential for AI to automate HSM management. There is also interest in the role of HSMs in securing AI models and data, particularly in machine learning environments where data privacy and model integrity are paramount. Users are keen to understand if AI can make HSMs more intelligent, adaptable, and efficient in threat detection and response.
Artificial intelligence is set to profoundly influence the Hardware Security Module market by both increasing the demand for HSMs and enhancing their operational capabilities. As AI systems become more pervasive, the critical data they process and the models they utilize become prime targets for cyberattacks, thus necessitating robust hardware-backed security. HSMs will play a crucial role in securing AI algorithms, machine learning models, and the vast datasets used for training, ensuring data integrity, confidentiality, and authentic execution environments for AI workloads. This includes securing the cryptographic keys that protect AI model parameters and sensitive input data.
Furthermore, AI can augment the functionality of HSMs by enabling more sophisticated threat detection, anomaly identification, and automated response mechanisms. AI-driven analytics can help in proactively identifying potential vulnerabilities or unusual access patterns related to cryptographic key usage, allowing for quicker mitigation. Conversely, the rise of AI-driven cyber threats, such as advanced phishing, deepfakes, and automated exploit generation, will necessitate even stronger, AI-resilient cryptographic foundations provided by HSMs. This dual impact positions AI as a significant catalyst for innovation and demand within the HSM market.
- Increased demand for HSMs to secure AI models, training data, and inferences against tampering and unauthorized access.
- HSMs provide a trusted execution environment for sensitive AI operations, protecting cryptographic keys used in AI systems.
- AI-powered analytics can enhance HSM monitoring for anomalies in key usage, improving threat detection and response.
- Automation of HSM management and configuration through AI for optimized performance and reduced human error.
- Development of AI-resilient cryptographic algorithms within HSMs to counter AI-driven cyberattacks.
- Securing the supply chain of AI hardware and software components using HSMs for integrity verification.
Key Takeaways Hardware Security Module Market Size & Forecast
Common user questions regarding the key takeaways from the Hardware Security Module (HSM) market size and forecast often focus on understanding the primary drivers of growth, the most significant emerging trends, and the long-term prospects of the market. Users are interested in identifying the sectors or applications that will fuel the most substantial growth, the impact of regulatory changes, and how the market is preparing for future technological shifts like quantum computing. They seek concise summaries that highlight the most impactful insights for strategic planning and investment decisions.
The Hardware Security Module market is poised for substantial expansion, driven predominantly by the escalating global cybersecurity landscape and the imperative for organizations to comply with evolving data protection regulations. The forecast period anticipates strong growth, underpinned by the increasing adoption of cloud computing, the proliferation of IoT devices, and the growing complexity of cyber threats. This growth signifies a foundational shift towards hardware-backed security as a non-negotiable component of enterprise IT infrastructure, moving beyond traditional software-only approaches.
- The market is projected for robust growth, indicating increasing enterprise reliance on hardware-based security.
- Stringent regulatory compliance and data breach prevention are primary growth catalysts for HSM adoption.
- Cloud-based HSMs and HSM-as-a-Service models represent a significant share of future market expansion.
- Investment in quantum-safe cryptography within HSMs is becoming a strategic imperative for long-term security.
- Emerging applications in blockchain, IoT, and critical infrastructure are driving diversified demand for HSMs.
Hardware Security Module Market Drivers Analysis
The Hardware Security Module market is primarily propelled by the ever-increasing sophistication and frequency of cyberattacks, which necessitate more robust and tamper-resistant security solutions for cryptographic key management. Organizations across various sectors are recognizing that software-only security measures are insufficient against advanced persistent threats and zero-day exploits. This realization drives the adoption of HSMs to establish a hardware root of trust, ensuring the integrity and confidentiality of sensitive data and digital identities. The inherent security advantages of HSMs, such as physical tamper resistance and dedicated cryptographic processing, make them indispensable in securing critical infrastructure and sensitive operations.
Another significant driver is the global landscape of stringent regulatory and compliance mandates. Regulations like GDPR, HIPAA, PCI DSS, and various national cybersecurity frameworks require organizations to implement robust data protection measures, often specifically referencing the need for hardware-based cryptographic key protection. The fear of heavy penalties for non-compliance and the potential reputational damage from data breaches compel businesses to invest in HSMs. Furthermore, the rapid expansion of cloud computing and digital transformation initiatives across industries necessitates secure key management for protecting data in distributed environments, leading to increased demand for cloud-based HSM solutions and services.
| Drivers | (~) Impact on CAGR % Forecast | Regional/Country Relevance | Impact Time Period |
|---|---|---|---|
| Increasing Cyberattacks and Data Breaches | +2.5% | Global, particularly North America, Europe, Asia Pacific | 2025-2033 (Long-term) |
| Stringent Regulatory Compliance (e.g., GDPR, HIPAA, PCI DSS) | +2.0% | Global, especially EU, US, UK, Australia | 2025-2030 (Mid-term) |
| Rising Adoption of Cloud Computing and Digital Transformation | +1.8% | Global, particularly North America, Asia Pacific | 2025-2033 (Long-term) |
| Proliferation of IoT Devices and Connected Systems | +1.5% | Global, especially China, US, Germany | 2027-2033 (Long-term) |
| Growth in Blockchain and Distributed Ledger Technologies (DLT) | +1.0% | Global, particularly North America, Europe, Singapore | 2026-2033 (Long-term) |
Hardware Security Module Market Restraints Analysis
Despite the strong growth drivers, the Hardware Security Module market faces several notable restraints. A primary concern is the relatively high initial cost associated with acquiring and deploying HSMs, particularly for smaller and medium-sized enterprises (SMEs). This significant upfront investment in hardware, software licenses, and integration services can be a barrier to entry, especially when compared to less secure but more affordable software-based cryptographic solutions. Furthermore, the operational complexity involved in managing HSMs, including key lifecycle management, regular audits, and maintaining compliance, often requires specialized technical expertise, which can be scarce and expensive to acquire.
Another restraint stems from the complexity of integrating HSMs into existing IT infrastructures. Legacy systems and diverse application environments can pose significant integration challenges, requiring extensive customization and professional services. This complexity can lead to prolonged deployment times and increased project costs, deterring some organizations from adopting HSM technology. Additionally, organizations might perceive a lack of flexibility or scalability with on-premise HSM solutions, preferring the perceived agility of purely software-defined security, although the rise of cloud-based HSM-as-a-Service is mitigating this concern to some extent.
| Restraints | (~) Impact on CAGR % Forecast | Regional/Country Relevance | Impact Time Period |
|---|---|---|---|
| High Initial Cost and Total Cost of Ownership (TCO) | -1.2% | Global, particularly SMEs in developing regions | 2025-2030 (Mid-term) |
| Complexity of Integration and Management | -1.0% | Global, across all enterprise sizes | 2025-2030 (Mid-term) |
| Lack of Skilled Personnel for Deployment and Maintenance | -0.8% | Global, acute in emerging economies | 2025-2033 (Long-term) |
| Limited Awareness Among SMEs Regarding HSM Benefits | -0.5% | Asia Pacific, Latin America, MEA | 2025-2028 (Short-term) |
Hardware Security Module Market Opportunities Analysis
The Hardware Security Module market presents significant opportunities for growth, particularly with the advent of post-quantum cryptography (PQC). As quantum computing capabilities advance, existing cryptographic algorithms face the threat of being compromised. This creates a pressing need for HSMs capable of supporting quantum-safe algorithms, driving a new wave of demand for cryptographic modernization. Vendors that can successfully integrate and offer PQC-ready HSMs will gain a substantial competitive advantage, serving governments, financial institutions, and critical infrastructure that require future-proof security solutions. This transition represents a major upgrade cycle and a long-term revenue stream for the market.
Another substantial opportunity lies in the expanding adoption of blockchain and distributed ledger technologies (DLT). HSMs are crucial for securing the private keys used in blockchain transactions, managing digital identities, and ensuring the integrity of smart contracts. As blockchain continues to gain traction across finance, supply chain, and healthcare, the demand for high-assurance, tamper-proof key storage solutions will skyrocket. Furthermore, the continuous growth of the Internet of Things (IoT) ecosystem, with billions of connected devices, creates a vast opportunity for HSMs to provide secure device identity, authentication, and data encryption at the edge, mitigating vulnerabilities inherent in large-scale IoT deployments. The move towards software-defined HSMs and micro-HSMs for edge computing also presents lucrative avenues for market expansion.
| Opportunities | (~) Impact on CAGR % Forecast | Regional/Country Relevance | Impact Time Period |
|---|---|---|---|
| Emergence of Post-Quantum Cryptography (PQC) | +1.5% | Global, particularly developed economies | 2028-2033 (Long-term) |
| Growing Adoption of Blockchain and DLT | +1.2% | Global, strong in North America, Europe, Asia Pacific | 2026-2033 (Long-term) |
| Expansion of IoT and Edge Computing Security Needs | +1.0% | Global, strong in Asia Pacific, North America | 2027-2033 (Long-term) |
| Rising Demand for Hardware Root of Trust in Supply Chains | +0.8% | Global, particularly manufacturing, defense | 2025-2030 (Mid-term) |
| Increasing Demand for Cloud-Based HSMs (HSM-as-a-Service) | +0.7% | Global, strong in North America, Europe | 2025-2033 (Long-term) |
Hardware Security Module Market Challenges Impact Analysis
The Hardware Security Module market faces several significant challenges that could impede its growth. One major challenge is the inherent complexity associated with integrating HSMs into diverse IT ecosystems. Organizations often operate with a heterogeneous mix of legacy systems, on-premise infrastructure, and various cloud platforms, making seamless integration of HSMs a technically intricate and time-consuming process. This complexity can lead to deployment delays, increased professional service costs, and potential compatibility issues, particularly for smaller organizations with limited IT resources or expertise. Ensuring interoperability across different vendor solutions and cloud environments also remains a persistent hurdle.
Another critical challenge is the rapidly evolving threat landscape. Cybercriminals are constantly developing more sophisticated attack methods, including advanced persistent threats (APTs), supply chain attacks, and side-channel attacks targeting hardware. While HSMs are designed to be highly secure, manufacturers must continuously innovate to protect against these evolving threats, which requires significant research and development investments. Furthermore, the shortage of skilled cybersecurity professionals who possess the expertise to deploy, configure, and manage HSMs effectively poses a substantial challenge globally. This talent gap can lead to improper implementations, underutilization of HSM capabilities, or increased reliance on external consultants, adding to operational costs and potential security vulnerabilities.
| Challenges | (~) Impact on CAGR % Forecast | Regional/Country Relevance | Impact Time Period |
|---|---|---|---|
| Integration Complexity with Diverse IT Infrastructures | -1.0% | Global, particularly enterprises with legacy systems | 2025-2030 (Mid-term) |
| Rapidly Evolving Cyber Threat Landscape | -0.9% | Global | 2025-2033 (Long-term) |
| Shortage of Skilled Cybersecurity Professionals | -0.8% | Global, acute in emerging economies | 2025-2033 (Long-term) |
| Supply Chain Security Concerns for Hardware Components | -0.6% | Global, especially sensitive sectors like government, defense | 2025-2030 (Mid-term) |
| Standardization Issues Across Different Vendor Solutions | -0.5% | Global | 2025-2028 (Short-term) |
Hardware Security Module Market - Updated Report Scope
This comprehensive report provides an in-depth analysis of the global Hardware Security Module (HSM) market, offering a detailed assessment of its current landscape, historical performance, and future growth trajectory. It covers key market dynamics, including drivers, restraints, opportunities, and challenges, along with a thorough segmentation analysis by type, deployment, application, and industry verticals. The report also highlights regional market insights and profiles leading industry players, providing a holistic view of the market's competitive landscape and strategic recommendations for stakeholders.
| Report Attributes | Report Details |
|---|---|
| Base Year | 2024 |
| Historical Year | 2019 to 2023 |
| Forecast Year | 2025 - 2033 |
| Market Size in 2025 | USD 1.5 billion |
| Market Forecast in 2033 | USD 3.8 billion |
| Growth Rate | 11.8% CAGR |
| Number of Pages | 247 |
| Key Trends |
|
| Segments Covered |
|
| Key Companies Covered | Thales Group, Utimaco GmbH, Entrust Corporation, Futurex LP, Yubico, nCipher Security (an Entrust Company), Atos SE (Eviden), Microchip Technology Inc., Cavium Inc. (Marvell Technology Group Ltd.), IBM Corporation, Hewlett Packard Enterprise (HPE), Google LLC (Google Cloud), Amazon Web Services (AWS), Microsoft Corporation (Azure), Gemalto (Thales Group), Infineon Technologies AG, Ledger SAS, Securosys SA, Swift (SWIFTNet), SafeNet (Thales Group) |
| Regions Covered | North America, Europe, Asia Pacific (APAC), Latin America, Middle East, and Africa (MEA) |
| Speak to Analyst | Avail customised purchase options to meet your exact research needs. Request For Analyst Or Customization |
Segmentation Analysis
The Hardware Security Module (HSM) market is extensively segmented to provide a granular view of its diverse applications and deployment models. This segmentation highlights the various types of HSMs available, their deployment environments, the specific use cases they address, and the industry verticals that are driving their adoption. Understanding these segments is crucial for identifying niche market opportunities and tailoring solutions to meet specific customer requirements across different sectors and technological landscapes.
The market's primary segmentation by type includes Network-Attached HSMs, offering centralized key management; PCIe-Based HSMs, favored for high-performance server environments; and USB-Based HSMs, providing portability and ease of use for smaller-scale applications. The deployment segment differentiates between traditional On-Premise installations, which offer maximum control, and the rapidly growing Cloud-Based (HSM-as-a-Service) models, which provide scalability and flexibility. Further segmentation by application illustrates the diverse cryptographic needs, ranging from payment processing and data encryption to securing emerging technologies like IoT and blockchain. Finally, the industry vertical breakdown reveals the varying levels of adoption and specific security requirements across sectors like BFSI, Government, IT & Telecom, and Healthcare, each presenting unique demands for HSM solutions.
- By Type:
- Network-Attached HSM
- PCIe-Based HSM
- USB-Based HSM
- By Deployment:
- On-Premise
- Cloud-Based (HSM-as-a-Service)
- By Application:
- Payment Processing
- Data Encryption
- Public Key Infrastructure (PKI)
- Identity & Access Management (IAM)
- Document Signing
- Code Signing
- Database Encryption
- IoT Security
- Blockchain Applications
- Other Applications
- By Industry Vertical:
- Banking, Financial Services, and Insurance (BFSI)
- Government & Public Sector
- IT & Telecommunication
- Healthcare & Life Sciences
- Retail & Consumer Goods
- Energy & Utilities
- Manufacturing
- Others
Regional Highlights
- North America: Dominates the market due to stringent regulatory compliance, high adoption of cloud computing, and a robust cybersecurity infrastructure, particularly in the US and Canada. Significant investments in data centers and digital transformation drive demand.
- Europe: A strong market driven by comprehensive data protection regulations like GDPR and the increasing need for secure digital identities. Countries such as Germany, the UK, and France are key contributors, focusing on banking, government, and automotive sectors.
- Asia Pacific (APAC): Emerging as the fastest-growing region, fueled by rapid digital transformation, increasing internet penetration, and escalating cyber threats in countries like China, India, Japan, and Australia. Significant investments in smart cities, IoT, and financial technologies are boosting HSM adoption.
- Latin America: Experiencing gradual growth, primarily driven by increasing digitalization, e-commerce, and the need for secure online transactions in economies like Brazil and Mexico. Regulatory pressures are also contributing to market expansion.
- Middle East and Africa (MEA): Shows promising growth with rising awareness of cybersecurity risks, government initiatives for digital economy development, and investments in critical infrastructure, particularly in the UAE, Saudi Arabia, and South Africa.
Top Key Players
The market research report includes a detailed profile of leading stakeholders in the Hardware Security Module Market.- Thales Group
- Utimaco GmbH
- Entrust Corporation
- Futurex LP
- Yubico
- nCipher Security (an Entrust Company)
- Atos SE (Eviden)
- Microchip Technology Inc.
- Marvell Technology Group Ltd.
- IBM Corporation
- Hewlett Packard Enterprise (HPE)
- Google LLC (Google Cloud)
- Amazon Web Services (AWS)
- Microsoft Corporation (Azure)
- Infineon Technologies AG
- Ledger SAS
- Securosys SA
- SWIFT
- Qrypt
- Quantum Xchange
Frequently Asked Questions
What is a Hardware Security Module (HSM) and why is it important?
A Hardware Security Module (HSM) is a physical computing device that safeguards and manages digital keys for strong authentication and provides cryptoprocessing. It is crucial because it offers a tamper-resistant environment for cryptographic operations, protecting sensitive keys from unauthorized access, software vulnerabilities, and physical attacks, thus ensuring data integrity, confidentiality, and authenticity in critical applications.
How does an HSM secure cryptographic keys?
An HSM secures cryptographic keys by storing them in a hardened, tamper-resistant hardware environment. It performs cryptographic operations within its secure boundary, ensuring keys are never exposed in clear text outside the module. HSMs often employ physical security measures, secure key generation, secure key storage, and strict access controls to prevent key compromise.
What are the primary applications of HSMs in enterprise environments?
HSMs are used across various enterprise applications including Public Key Infrastructure (PKI), secure payment processing, data encryption (for databases, files, and cloud storage), code signing, document signing, identity and access management (IAM), secure boot processes, and securing blockchain applications and IoT device identities.
What is the difference between an on-premise HSM and a cloud-based HSM-as-a-Service?
An on-premise HSM is a physical appliance deployed and managed within an organization's own data center, offering maximum control and often meeting specific compliance requirements. A cloud-based HSM-as-a-Service, provided by cloud vendors, allows organizations to utilize HSM functionality without owning or managing the hardware, offering scalability, flexibility, and reduced operational overhead, suitable for cloud-native applications and hybrid environments.
How will post-quantum cryptography (PQC) impact the HSM market?
Post-quantum cryptography (PQC) will significantly impact the HSM market by driving demand for next-generation HSMs capable of supporting quantum-safe algorithms. As quantum computers pose a theoretical threat to current cryptographic standards, organizations will need to upgrade their cryptographic infrastructure to PQC-ready HSMs to maintain long-term data security, creating a major market opportunity for vendors offering future-proof solutions.

