Hardware Encryption Device Market
Hardware Encryption Device Market Size, Scope, Growth, Trends and By Segmentation Types, Applications, Regional Analysis and Industry Forecast (2025-2033)
Report ID : RI_704397 | Last Updated : August 05, 2025 |
Format : ![]()
![]()
![]()
![]()
Hardware Encryption Device Market Size
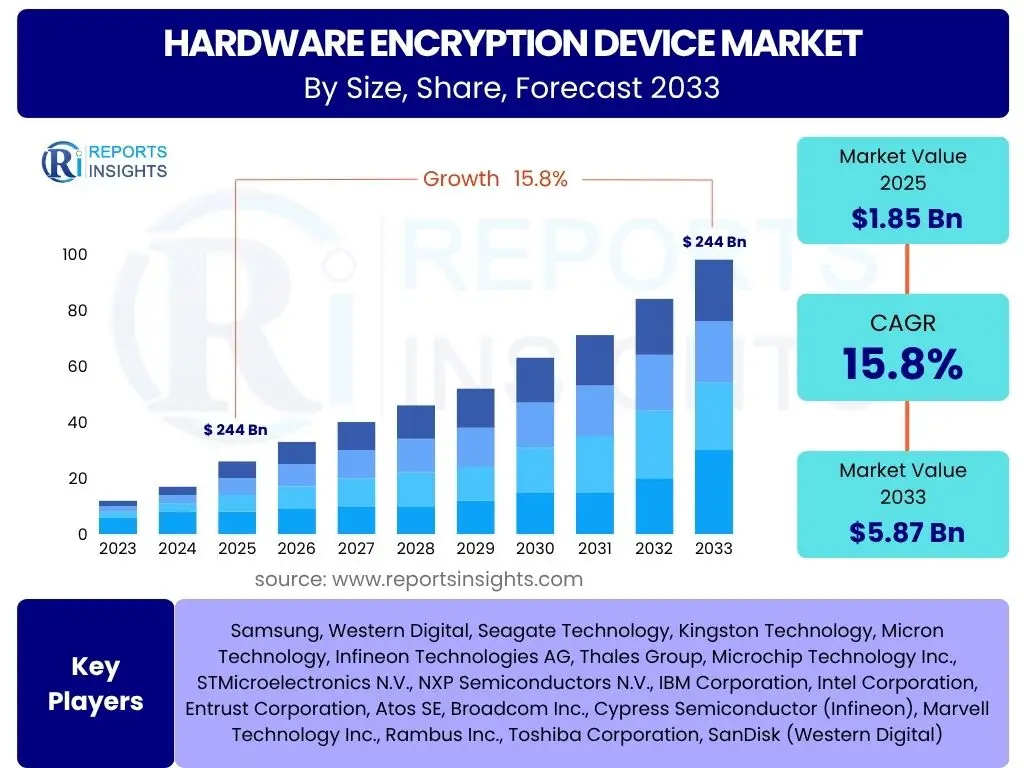
According to Reports Insights Consulting Pvt Ltd, The Hardware Encryption Device Market is projected to grow at a Compound Annual Growth Rate (CAGR) of 15.8% between 2025 and 2033. The market is estimated at USD 1.85 billion in 2025 and is projected to reach USD 5.87 billion by the end of the forecast period in 2033.
Key Hardware Encryption Device Market Trends & Insights
Current market dynamics for hardware encryption devices are significantly influenced by the escalating global threat landscape, which necessitates robust and resilient data protection mechanisms. Users frequently inquire about the latest advancements in encryption technologies, the integration of these devices within complex IT infrastructures, and their adaptability to emerging security paradigms such as Zero Trust architectures. There is a strong interest in understanding how hardware solutions are evolving to meet demands for both enhanced security and operational efficiency, particularly in the context of remote workforces and widespread cloud adoption.
The convergence of increasing regulatory pressures and the proliferation of sensitive data across diverse environments is driving innovation in the hardware encryption sector. Market participants are observing a shift towards more integrated and compact solutions that offer seamless deployment and management. Furthermore, the longevity and future-proofing capabilities of these devices, especially against the backdrop of quantum computing advancements, are becoming critical considerations for enterprises. These trends collectively underscore a market moving towards more sophisticated, versatile, and forward-looking security solutions.
- Miniaturization and integration of encryption capabilities directly into endpoints and embedded systems.
- Increased demand for FIPS 140-2 validated hardware encryption for regulatory compliance.
- Growing adoption of Hardware Security Modules (HSMs) and Trusted Platform Modules (TPMs) across various industries.
- Emergence of quantum-safe cryptography standards driving research and development in hardware encryption.
- Greater emphasis on seamless integration with cloud environments and multi-cloud strategies.
- Development of self-encrypting drives (SEDs) with enhanced management features.
- Expansion of hardware encryption use cases in IoT, Industrial IoT (IIoT), and edge computing devices.
- Focus on tamper-resistant designs and physical security features for hardware devices.
- Integration with Zero Trust security frameworks for stronger access control and data segmentation.
AI Impact Analysis on Hardware Encryption Device
Users frequently express curiosity regarding the transformative potential of Artificial Intelligence (AI) on hardware encryption devices. Common questions revolve around how AI can enhance the security and functionality of these devices, as well as the potential risks AI might introduce to cryptographic systems. The primary expectation is that AI will bolster defensive capabilities, making encryption hardware more intelligent, adaptive, and resilient against sophisticated cyber threats. There is also interest in AI's role in optimizing the performance and management of encryption keys and processes, thereby reducing human error and operational overheads.
Conversely, concerns exist about the potential for AI to be leveraged by malicious actors to compromise encryption. This includes the possibility of AI-driven side-channel attacks or the exploitation of vulnerabilities through advanced analytical techniques. Therefore, a critical theme in user queries is the development of AI-hardened encryption hardware that can not only leverage AI for its own defense but also resist AI-powered attacks. The consensus leans towards a future where AI plays a dual role: significantly improving the intelligence and robustness of hardware encryption while simultaneously posing new challenges that necessitate constant innovation in defensive strategies.
- AI-driven anomaly detection and threat intelligence integrated into hardware security modules.
- Optimization of cryptographic key management and rotation through AI algorithms.
- Enhanced side-channel attack detection and mitigation using AI-powered analysis.
- Predictive maintenance and proactive security health monitoring for hardware encryption devices via AI.
- Potential for AI to identify and exploit subtle vulnerabilities in hardware implementations, driving the need for more robust designs.
- Development of AI-hardened cryptographic primitives to resist AI-assisted cryptanalysis.
- AI-enabled adaptive security policies for dynamic access control based on contextual data.
Key Takeaways Hardware Encryption Device Market Size & Forecast
Analysis of common user questions regarding the hardware encryption device market size and forecast reveals a predominant interest in understanding the underlying drivers of growth and the long-term viability of these solutions in an evolving cyber landscape. Users are keen to identify the primary market accelerators, such as escalating cyber threats and regulatory mandates, and how these factors translate into tangible market expansion. There is also significant curiosity about the projected trajectory of market valuation and the specific segments anticipated to exhibit the most robust growth over the forecast period.
The insights derived from these inquiries highlight that the market is poised for sustained and significant expansion, driven by an inherent and increasing global need for advanced data protection. Key takeaways emphasize the critical role of hardware encryption in achieving data sovereignty and compliance, particularly for sensitive sectors. The forecast indicates that integrated, high-performance, and future-proof solutions will command a premium, reflecting a strategic shift towards preventative security measures. Overall, the market's future is characterized by continuous innovation aimed at countering sophisticated threats and meeting stringent regulatory requirements.
- The market is experiencing robust double-digit growth, underscoring the critical need for advanced data security solutions.
- Regulatory compliance and the increasing volume of data breaches are primary catalysts for market expansion.
- Significant investment is expected in secure enterprise data solutions, including cloud and IoT environments.
- The shift towards integrated hardware security components (e.g., TPMs, HSMs, secure enclaves) is a defining trend.
- Long-term market stability is supported by continuous threats and the non-negotiable requirement for data privacy.
- Emerging economies present substantial growth opportunities due to accelerating digital transformation initiatives.
Hardware Encryption Device Market Drivers Analysis
The hardware encryption device market is propelled by a confluence of critical factors, primarily the escalating frequency and sophistication of cyberattacks, which underscore the necessity for impenetrable data protection. As organizations worldwide grapple with the severe financial and reputational consequences of data breaches, the proactive adoption of hardware-based encryption becomes an imperative. This driver is further amplified by a progressively stringent global regulatory landscape, wherein mandates such as GDPR, CCPA, and HIPAA impose severe penalties for non-compliance related to data security, making hardware encryption a foundational element for adherence.
Beyond compliance and threat mitigation, the explosive growth of the Internet of Things (IoT) and the pervasive shift towards cloud computing environments are creating unprecedented demand for secure endpoints and cloud data protection. IoT devices, often deployed in vulnerable environments, require robust, immutable security at the hardware level, while cloud adoption necessitates powerful encryption to protect data in transit and at rest across diverse architectures. These factors collectively highlight a market driven by an urgent need for enhanced security, regulatory conformity, and the protection of expanding digital ecosystems.
| Drivers | (~) Impact on CAGR % Forecast | Regional/Country Relevance | Impact Time Period |
|---|---|---|---|
| Increasing Data Breaches and Cyberattacks | +1.5% | Global | Short-term to Mid-term (2025-2029) |
| Stringent Regulatory Compliance and Data Privacy Laws | +2.0% | Global (Europe, North America, Asia Pacific) | Long-term (2025-2033) |
| Proliferation of IoT and Connected Devices | +1.0% | Asia Pacific, North America | Mid-term (2027-2031) |
| Growing Adoption of Cloud-Based Services | +1.0% | Global | Mid-term (2026-2030) |
| Demand for High-Performance and Tamper-Resistant Security | +0.5% | North America, Europe | Short-term (2025-2028) |
Hardware Encryption Device Market Restraints Analysis
Despite the compelling drivers for market growth, the hardware encryption device market faces several significant restraints that could impede its expansion. One primary challenge is the relatively high upfront cost of implementing hardware encryption solutions compared to software-only alternatives. This cost can be prohibitive for small and medium-sized enterprises (SMBs) and organizations with limited IT budgets, slowing down adoption, especially in price-sensitive emerging markets. While the long-term benefits in terms of security and compliance are substantial, the initial investment often acts as a deterrent.
Another crucial restraint is the inherent complexity associated with the integration and management of diverse hardware encryption devices within existing IT infrastructures. Enterprises often struggle with ensuring interoperability across different platforms and managing cryptographic keys effectively, leading to deployment delays and potential operational hurdles. Furthermore, a general lack of awareness regarding the distinct advantages of hardware encryption over software solutions, coupled with a shortage of skilled personnel capable of deploying and maintaining these sophisticated systems, contributes to slowed market penetration. These factors collectively highlight the need for simpler, more cost-effective, and user-friendly solutions to overcome existing market barriers.
| Restraints | (~) Impact on CAGR % Forecast | Regional/Country Relevance | Impact Time Period |
|---|---|---|---|
| High Cost of Implementation and Maintenance | -0.8% | Emerging Markets, SMBs Globally | Mid-term (2025-2030) |
| Complexity of Integration with Existing IT Infrastructure | -0.5% | Global, Particularly Legacy Systems | Short-term (2025-2028) |
| Lack of Awareness and Skilled Personnel | -0.3% | Global | Short-term to Mid-term (2025-2029) |
| Supply Chain Vulnerabilities and Geopolitical Risks | -0.4% | Global | Short-term (2025-2027) |
Hardware Encryption Device Market Opportunities Analysis
The hardware encryption device market is poised for significant growth stemming from several emerging opportunities. A paramount opportunity arises from the looming threat of quantum computing, which promises to render current cryptographic algorithms vulnerable. This necessitates the development and widespread adoption of post-quantum cryptography (PQC) solutions embedded directly into hardware, creating a new wave of demand for quantum-safe encryption devices. Furthermore, the increasing integration of secure enclaves within central processing units (CPUs) and System-on-Chips (SoCs) offers a pervasive and highly secure method for protecting sensitive data and workloads at the silicon level, opening new markets for silicon-level security solutions.
The rapid expansion of Industrial IoT (IIoT) across manufacturing, energy, and logistics sectors presents a fertile ground for hardware encryption. IIoT devices, often operating in critical infrastructure, require robust, physically tamper-resistant encryption from the ground up to secure operational technology (OT) environments. Moreover, the general growth in demand for enhanced cybersecurity in critical infrastructure, spanning sectors like finance, utilities, and defense, continues to create substantial opportunities for specialized hardware encryption solutions. Finally, the growing need for privacy in consumer electronics, such as smartphones, smart home devices, and wearables, offers a vast, untapped market for embedded hardware encryption, enabling device manufacturers to differentiate their products with superior security features.
| Opportunities | (~) Impact on CAGR % Forecast | Regional/Country Relevance | Impact Time Period |
|---|---|---|---|
| Emergence of Quantum Computing and Post-Quantum Cryptography | +1.2% | Global, particularly developed economies | Long-term (2028-2033) |
| Development of Secure Enclaves in CPUs and SoCs | +0.7% | North America, Europe, Asia Pacific | Mid-term (2026-2031) |
| Growth in Industrial IoT (IIoT) and Operational Technology (OT) Security | +0.8% | Asia Pacific, Europe | Mid-term (2027-2032) |
| Increased Adoption in Critical Infrastructure Protection | +0.6% | Global | Long-term (2029-2033) |
| Expansion into Consumer Electronics for Data Privacy | +0.5% | Asia Pacific, North America | Mid-term (2026-2030) |
Hardware Encryption Device Market Challenges Impact Analysis
The hardware encryption device market, while promising, faces several inherent challenges that can constrain its growth and widespread adoption. The continuously evolving threat landscape, characterized by increasingly sophisticated attack vectors, zero-day exploits, and advanced persistent threats (APTs), demands constant innovation in hardware security. Staying ahead of these agile adversaries requires significant research and development investments, which can be a financial burden for manufacturers and may still result in security solutions that become outdated quickly.
Another significant challenge is ensuring interoperability across a diverse ecosystem of hardware, software, and cloud platforms. Different vendors and technologies often use proprietary implementations or varying standards, leading to compatibility issues that complicate deployment and management for end-users. This lack of seamless integration can create security gaps or operational inefficiencies. Furthermore, the global shortage of skilled cybersecurity professionals, particularly those with expertise in hardware-level security and cryptography, poses a significant impediment to the effective implementation and maintenance of these complex devices. Finally, regulatory fragmentation, where different regions or countries have distinct and often conflicting data privacy and security mandates, can create compliance complexities for multinational organizations, making a unified hardware encryption strategy difficult to implement.
| Challenges | (~) Impact on CAGR % Forecast | Regional/Country Relevance | Impact Time Period |
|---|---|---|---|
| Rapidly Evolving Threat Landscape and Attack Vectors | -0.6% | Global | Ongoing (2025-2033) |
| Interoperability Issues with Diverse IT Ecosystems | -0.5% | Global | Mid-term (2025-2030) |
| Shortage of Skilled Cybersecurity Personnel | -0.7% | Global | Long-term (2025-2033) |
| Regulatory Fragmentation and Compliance Complexities | -0.4% | Global | Ongoing (2025-2033) |
Hardware Encryption Device Market - Updated Report Scope
This report offers an in-depth analysis of the global Hardware Encryption Device Market, providing a comprehensive overview of its size, growth trajectory, key trends, and future projections. It segments the market extensively by various types, interfaces, end-use industries, applications, and deployment models to provide granular insights. The scope encompasses detailed regional analysis, identifying prominent growth drivers, restraints, opportunities, and challenges influencing market dynamics. Furthermore, the report profiles leading market players, offering a competitive landscape analysis essential for strategic decision-making within the hardware encryption sector.
| Report Attributes | Report Details |
|---|---|
| Base Year | 2024 |
| Historical Year | 2019 to 2023 |
| Forecast Year | 2025 - 2033 |
| Market Size in 2025 | USD 1.85 billion |
| Market Forecast in 2033 | USD 5.87 billion |
| Growth Rate | 15.8% |
| Number of Pages | 245 |
| Key Trends |
|
| Segments Covered |
|
| Key Companies Covered | Samsung, Western Digital, Seagate Technology, Kingston Technology, Micron Technology, Infineon Technologies AG, Thales Group, Microchip Technology Inc., STMicroelectronics N.V., NXP Semiconductors N.V., IBM Corporation, Intel Corporation, Entrust Corporation, Atos SE, Broadcom Inc., Cypress Semiconductor (Infineon), Marvell Technology Inc., Rambus Inc., Toshiba Corporation, SanDisk (Western Digital) |
| Regions Covered | North America, Europe, Asia Pacific (APAC), Latin America, Middle East, and Africa (MEA) |
| Speak to Analyst | Avail customised purchase options to meet your exact research needs. Request For Analyst Or Customization |
Segmentation Analysis
The hardware encryption device market is meticulously segmented to provide a granular understanding of its diverse components and their respective contributions to overall market dynamics. This detailed segmentation enables stakeholders to identify specific growth areas, understand demand patterns across various applications, and recognize the predominant technologies and form factors driving adoption. By dissecting the market along multiple parameters, this analysis offers a comprehensive view of where demand is concentrated and how different segments are evolving in response to technological advancements and market needs.
- By Type: Includes USB Drives, External Hard Drives (HDD), Internal Hard Drives (HDD), Solid State Drives (SSD), Chipset (encompassing Trusted Platform Modules - TPMs, Hardware Security Modules - HSMs, and Secure Enclaves), Network Attached Storage (NAS), and Other specialized devices.
- By Interface: Covers prevalent connectivity standards such as USB, SATA, SAS, PCIe, Fibre Channel, Ethernet/Network, and proprietary interfaces specific to certain devices.
- By End-Use Industry: Categorizes adoption across key sectors including Banking, Financial Services and Insurance (BFSI), Government and Defense, Healthcare and Life Sciences, IT and Telecommunications, Retail and E-commerce, Manufacturing, Automotive, Education, and other emerging industries.
- By Application: Details the primary use cases such as Data Protection, Network Security, Cloud Security, IoT Security, Payment Security, and Critical Infrastructure Protection.
- By Deployment: Distinguishes between On-Premise, Cloud, and Hybrid deployment models, reflecting varied organizational infrastructure strategies.
Regional Highlights
- North America: Dominates the market share due to the early adoption of advanced security technologies, stringent regulatory frameworks (e.g., HIPAA, GLBA, CCPA), and the presence of major technology and cybersecurity companies. High incidence of cyberattacks and a strong focus on data privacy further accelerate market growth.
- Europe: A significant market driven by robust data protection regulations such as GDPR, which mandates strict data encryption practices. Countries like Germany, the UK, and France are leading in adopting hardware encryption devices across BFSI, government, and healthcare sectors, prioritizing compliance and robust data security.
- Asia Pacific (APAC): Expected to exhibit the highest growth rate owing to rapid digitalization, increasing internet penetration, burgeoning IoT ecosystems, and growing awareness about cybersecurity in countries like China, India, Japan, and South Korea. Government initiatives to enhance digital infrastructure and cybersecurity are also key drivers.
- Latin America: An emerging market for hardware encryption, experiencing increasing cyber threats and growing awareness about data protection. Countries like Brazil and Mexico are investing in digital transformation, creating new opportunities for hardware encryption solutions, albeit at a slower pace than developed regions.
- Middle East and Africa (MEA): Shows promising growth driven by significant investments in critical infrastructure, smart city initiatives, and diversification of economies away from oil. Cybersecurity is a growing priority for governments and enterprises in the region, leading to increased adoption of advanced security solutions.
Top Key Players
The market research report includes a detailed profile of leading stakeholders in the Hardware Encryption Device Market.- Samsung
- Western Digital
- Seagate Technology
- Kingston Technology
- Micron Technology
- Infineon Technologies AG
- Thales Group
- Microchip Technology Inc.
- STMicroelectronics N.V.
- NXP Semiconductors N.V.
- IBM Corporation
- Intel Corporation
- Entrust Corporation
- Atos SE
- Broadcom Inc.
- Cypress Semiconductor (Infineon)
- Marvell Technology Inc.
- Rambus Inc.
- Toshiba Corporation
- SanDisk (Western Digital)
Frequently Asked Questions
What is hardware encryption and why is it important?
Hardware encryption involves the use of dedicated physical components, such as chips or processors, to perform cryptographic operations. It is crucial because it offers a higher level of security, speed, and integrity compared to software-based encryption. Hardware encryption protects data even if the operating system is compromised or tampered with, and often includes features like tamper detection and protection against side-channel attacks, making it essential for safeguarding sensitive information against sophisticated threats and ensuring regulatory compliance.
How does hardware encryption differ from software encryption?
The primary difference lies in their execution and security posture. Hardware encryption uses dedicated physical chips or devices to encrypt data, keeping cryptographic keys isolated and secure from the main system’s vulnerabilities. This offers superior protection against malware, unauthorized access, and physical tampering, often with minimal performance impact. Software encryption, conversely, relies on a computer's operating system and CPU, making it susceptible to software vulnerabilities, memory attacks, and slower performance due to shared system resources. Hardware encryption provides a more robust and resilient security foundation.
Which industries benefit most from hardware encryption devices?
Industries handling highly sensitive data or operating under stringent regulatory requirements derive the greatest benefits from hardware encryption. This includes Banking, Financial Services, and Insurance (BFSI) for transaction security, Government and Defense for classified information, Healthcare for patient data privacy (e.g., HIPAA compliance), and IT & Telecommunications for network infrastructure and cloud data protection. Any sector facing high-value cyber threats or mandatory data protection laws finds hardware encryption indispensable for compliance and robust security.
What are the primary types of hardware encryption devices available?
The market offers various types of hardware encryption devices tailored for different applications. Common types include Self-Encrypting Drives (SEDs) like internal and external HDDs and SSDs, which encrypt data directly on the drive. USB drives with built-in encryption offer portable security. Chipset-based solutions such as Trusted Platform Modules (TPMs) provide root of trust and secure boot capabilities, while Hardware Security Modules (HSMs) are high-security cryptographic processors for key management and strong authentication, often used in data centers and cloud environments. Network Attached Storage (NAS) devices also often integrate hardware encryption for stored data.
How is the threat of quantum computing addressed by hardware encryption?
The threat of quantum computing to current cryptographic standards is being addressed through the development of Post-Quantum Cryptography (PQC) solutions, which are algorithms designed to withstand quantum attacks. Hardware encryption devices are crucial for implementing PQC effectively because they can embed these new, more complex algorithms directly into silicon, ensuring high performance and tamper resistance. Research and development efforts are focused on creating quantum-safe hardware security modules and secure enclaves that can protect cryptographic keys and perform quantum-resistant encryption, future-proofing data security against emerging quantum threats.

