Embedded Security Market
Embedded Security Market Size, Scope, Growth, Trends and By Segmentation Types, Applications, Regional Analysis and Industry Forecast (2025-2033)
Report ID : RI_704551 | Last Updated : August 11, 2025 |
Format : ![]()
![]()
![]()
![]()
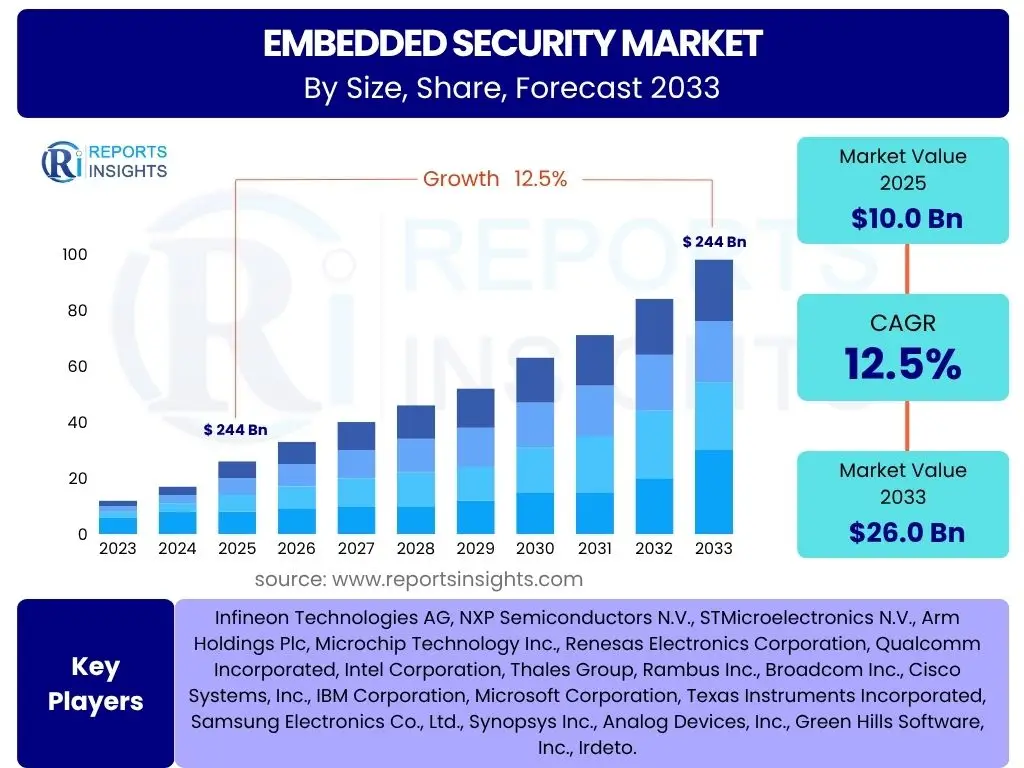
Embedded Security Market Size
According to Reports Insights Consulting Pvt Ltd, The Embedded Security Market is projected to grow at a Compound Annual Growth Rate (CAGR) of 12.5% between 2025 and 2033. The market is estimated at USD 10.0 Billion in 2025 and is projected to reach USD 26.0 Billion by the end of the forecast period in 2033.
Key Embedded Security Market Trends & Insights
The Embedded Security Market is currently experiencing a significant transformation driven by the pervasive integration of connected devices across virtually all sectors. User inquiries frequently highlight the rapid expansion of the Internet of Things (IoT) and automotive industries as primary catalysts for enhanced security solutions. There is a growing understanding that traditional perimeter-based security is insufficient for embedded systems, leading to increased interest in hardware-rooted security, secure boot mechanisms, and secure over-the-air updates.
Another prominent trend gaining user attention is the convergence of operational technology (OT) and information technology (IT) security, particularly in industrial settings. This convergence necessitates robust embedded security measures to protect critical infrastructure from cyber threats. Furthermore, the imperative for regulatory compliance, such as GDPR and region-specific automotive security standards, is compelling manufacturers to embed security from the design phase rather than as an afterthought. This proactive approach is essential for mitigating risks and ensuring data integrity in sensitive applications.
Finally, the advent of edge computing and the increasing sophistication of cyberattacks are pushing the demand for more advanced embedded security features, including artificial intelligence and machine learning-powered threat detection at the device level. Users are keen on understanding how these advanced technologies can offer real-time protection against zero-day exploits and polymorphic malware, effectively safeguarding the growing landscape of interconnected embedded devices from diverse and evolving cyber threats.
- Proliferation of IoT and connected devices driving demand for foundational security.
- Rising adoption of hardware-rooted security (e.g., TPM, HSM, Secure Enclaves) for stronger protection.
- Increasing focus on secure over-the-air (OTA) updates and secure boot processes.
- Convergence of IT and OT security, emphasizing protection of industrial control systems.
- Strict regulatory compliance (e.g., GDPR, automotive standards) mandating security-by-design.
- Growth of edge computing necessitating distributed embedded security architectures.
- Integration of AI and machine learning for proactive threat detection and anomaly identification.
- Escalating sophistication of cyberattacks targeting embedded vulnerabilities.
- Emphasis on supply chain security for embedded components and software.
- Development of post-quantum cryptography (PQC) solutions for future-proofing embedded systems.
AI Impact Analysis on Embedded Security
User questions regarding the impact of Artificial Intelligence (AI) on embedded security frequently revolve around its dual nature: AI as a powerful tool for enhancing security defenses and AI as a potential vector for new, more sophisticated attacks. On the positive side, users are keen to understand how AI and machine learning algorithms can significantly improve threat detection capabilities within resource-constrained embedded environments. AI enables anomaly detection, predicting potential vulnerabilities, and identifying novel attack patterns in real time, far beyond the capabilities of traditional signature-based methods. This leads to more responsive and intelligent embedded security systems.
Conversely, concerns are raised about the potential for AI to be exploited by malicious actors. Users worry about adversarial AI attacks that could bypass security mechanisms, or the use of AI to automate and scale attack campaigns against embedded systems. The complexity of AI models can also introduce new vulnerabilities if not rigorously secured, posing challenges for validation and verification in safety-critical embedded applications. This necessitates robust AI security practices, including securing AI models themselves and the data pipelines they rely on.
Ultimately, the consensus among user inquiries points towards AI becoming an indispensable component of future embedded security strategies. It is expected to drive advancements in areas like predictive maintenance for security, automated vulnerability assessment, and adaptive defense mechanisms. However, this integration requires a proactive approach to secure AI itself, ensuring that its benefits outweigh the risks and that embedded systems can leverage AI's power without introducing new critical security flaws.
- Enhanced threat detection: AI algorithms can identify subtle anomalies and zero-day threats in embedded device behavior.
- Predictive security: Machine learning models analyze vast datasets to predict potential vulnerabilities and attack vectors.
- Automated incident response: AI can trigger automated containment or mitigation actions upon detecting a breach.
- Reduced false positives: AI-driven analysis helps distinguish legitimate variations from actual security incidents, optimizing alert fatigue.
- Improved resource efficiency: Optimized AI models can run on low-power embedded devices for on-device security.
- Risk of adversarial AI: Attackers can manipulate AI models to bypass security or generate sophisticated attacks.
- Data privacy concerns: AI training requires vast amounts of data, raising privacy considerations for embedded systems.
- Complexity and interpretability: Debugging and understanding AI model decisions in security can be challenging.
- New attack surfaces: The AI model itself, its training data, and inferencing process can become targets.
- Accelerated vulnerability discovery: AI tools can assist in rapid identification of flaws in embedded code.
Key Takeaways Embedded Security Market Size & Forecast
Analysis of common user questions regarding the Embedded Security Market size and forecast reveals a strong interest in understanding the underlying drivers and long-term implications of this growth. The primary takeaway is that the market's significant projected Compound Annual Growth Rate (CAGR) is not merely a statistical projection but a reflection of fundamental shifts in how industries operate and how consumers interact with technology. The pervasive digitalization, particularly across automotive, industrial IoT, and consumer electronics, creates an ever-expanding attack surface, making embedded security an indispensable foundational requirement rather than an optional add-on. This sustained growth indicates a mature yet rapidly evolving demand landscape.
Furthermore, users are keen to grasp the economic impact of this growth. The projected increase in market valuation from USD 10.0 Billion in 2025 to USD 26.0 Billion by 2033 signifies substantial investment opportunities for technology providers, solution developers, and cybersecurity firms. This growth is underpinned by the increasing awareness among manufacturers and end-users alike about the severe consequences of security breaches in embedded systems, including financial losses, reputational damage, and even risks to human safety. The forecast signals a robust commitment across sectors to integrate advanced security measures from the chip level to the cloud.
Another critical insight derived from user queries is the emphasis on proactive security strategies. The market's upward trajectory is largely driven by a shift from reactive patching to security-by-design principles, where security is woven into the very fabric of embedded systems from their inception. This includes hardware-rooted trust, secure boot, and authenticated updates. The forecast suggests that this paradigm shift will continue to fuel innovation and demand for specialized embedded security solutions, ensuring that devices are resilient against evolving cyber threats throughout their entire lifecycle. The market's sustained growth underscores its pivotal role in enabling a secure and trustworthy digital future.
- The Embedded Security Market is poised for substantial growth, driven by increasing connectivity and digitalization across industries.
- Significant market valuation increase from USD 10.0 Billion in 2025 to USD 26.0 Billion by 2033 underscores its critical importance.
- Growth is primarily fueled by the proliferation of IoT, connected vehicles, and industrial automation, expanding the need for robust device protection.
- A shift towards security-by-design and hardware-rooted trust is a key enabler of market expansion.
- Regulatory mandates and rising awareness of cyber risks are compelling organizations to prioritize embedded security investments.
- The market presents lucrative opportunities for technology providers specializing in secure hardware, software, and services for embedded systems.
- Ongoing innovation in areas like AI-driven security and post-quantum cryptography will further accelerate market development.
- The long-term forecast indicates sustained demand as embedded systems become even more integral to daily life and critical infrastructure.
Embedded Security Market Drivers Analysis
The Embedded Security Market is experiencing significant propulsion from a confluence of factors that underscore the growing criticality of device-level protection. A primary driver is the explosive growth of the Internet of Things (IoT) across consumer, industrial, and enterprise applications. As billions of devices connect to networks, each presents a potential entry point for cyberattacks, making embedded security indispensable for data integrity, privacy, and operational continuity. The sheer volume and diversity of these devices necessitate scalable and robust security solutions built into the hardware and firmware from the outset.
Another major impetus comes from the automotive industry's rapid advancements towards connected and autonomous vehicles. Modern vehicles are essentially computers on wheels, integrating numerous embedded systems for infotainment, ADAS, telematics, and V2X communication. The potential for cyberattacks to compromise vehicle safety or privacy has led to stringent regulations and industry standards, compelling automotive manufacturers to prioritize advanced embedded security features throughout the vehicle lifecycle, from design to end-of-life.
Furthermore, the escalating sophistication and frequency of cyber threats globally, including ransomware, malware, and state-sponsored attacks, compel industries to fortify their embedded systems. Coupled with this, stringent regulatory compliance mandates, such as GDPR, CCPA, and industry-specific certifications, require robust security measures to protect sensitive data and critical infrastructure. These regulatory pressures incentivize organizations to invest in comprehensive embedded security solutions to avoid hefty fines and reputational damage, thereby driving market demand.
| Drivers | (~) Impact on CAGR % Forecast | Regional/Country Relevance | Impact Time Period |
|---|---|---|---|
| Proliferation of IoT and Connected Devices | +3.5% | Global, particularly North America, Asia Pacific | Short-term (2025-2028), Mid-term (2029-2033) |
| Increasing Adoption of Connected & Autonomous Vehicles | +2.8% | Europe, North America, Japan, China | Mid-term (2027-2033) |
| Rising Sophistication of Cyber Threats | +2.2% | Global | Short-term (2025-2028), Mid-term (2029-2033) |
| Stringent Regulatory Compliance and Data Privacy Laws | +1.9% | Europe, North America, India, China | Short-term (2025-2028) |
| Growing Demand for Industrial IoT (IIoT) Security | +2.1% | North America, Europe, China | Mid-term (2027-2033) |
Embedded Security Market Restraints Analysis
Despite the robust growth, the Embedded Security Market faces several significant restraints that could impede its full potential. A primary challenge is the inherent resource constraints of many embedded devices, particularly those in low-power or cost-sensitive applications. These devices often have limited processing power, memory, and battery life, making it difficult to implement sophisticated security measures that demand substantial computational resources. This trade-off between security and performance or cost can deter manufacturers from adopting comprehensive security solutions, especially in highly competitive markets where cost efficiency is paramount.
Another major restraint stems from the complexity of integrating advanced security features into diverse embedded ecosystems. The fragmentation of operating systems, hardware architectures, and communication protocols across various embedded applications creates a highly complex environment for security implementation. Developers often face challenges in ensuring interoperability and maintaining security across heterogeneous systems, leading to longer development cycles and higher integration costs. This complexity can be a barrier for smaller manufacturers or those lacking specialized cybersecurity expertise.
Furthermore, the lack of standardized security frameworks and certification processes for embedded systems also acts as a restraint. While efforts are being made, the absence of universally accepted benchmarks for embedded security can lead to inconsistent security postures across devices and industries. This makes it difficult for consumers and businesses to assess the true security level of embedded products, potentially undermining trust and slowing adoption of more secure, but possibly more expensive, solutions. Addressing these challenges through standardization and easier integration is crucial for the market's sustained expansion.
| Restraints | (~) Impact on CAGR % Forecast | Regional/Country Relevance | Impact Time Period |
|---|---|---|---|
| Resource Constraints of Embedded Devices | -1.5% | Global | Short-term (2025-2028) |
| High Cost of Implementing Advanced Security Solutions | -1.2% | Emerging Economies, SMBs Globally | Short-term (2025-2028) |
| Lack of Standardization and Interoperability | -1.0% | Global | Mid-term (2027-2033) |
| Complexity of Security Integration and Development | -0.8% | Global | Short-term (2025-2028) |
| Shortage of Skilled Cybersecurity Professionals | -0.7% | Global | Mid-term (2027-2033) |
Embedded Security Market Opportunities Analysis
The Embedded Security Market is ripe with numerous opportunities, driven by technological advancements and evolving market needs. One significant area of opportunity lies in the burgeoning field of edge computing, where processing and data storage occur closer to the data source rather than in a centralized cloud. As more intelligent decision-making moves to the edge, the need for robust, low-latency embedded security solutions becomes paramount to protect sensitive data and ensure the integrity of critical operations, opening new avenues for specialized hardware and software security offerings.
Another substantial opportunity is presented by the development and integration of 5G technology. The high bandwidth, low latency, and massive device connectivity offered by 5G networks will accelerate the deployment of advanced IoT and connected systems across various sectors, from smart cities to industrial automation. Securing these 5G-enabled embedded devices, particularly against new types of network-based attacks and supply chain vulnerabilities, will create a surge in demand for embedded security solutions tailored to the 5G ecosystem, including advanced authentication and encryption protocols.
Furthermore, the emerging threat of quantum computing poses both a challenge and a significant opportunity for the embedded security market. As quantum computers capable of breaking current cryptographic standards become a reality, there will be an urgent need for post-quantum cryptography (PQC) solutions to secure embedded systems for the long term. Companies that can develop and implement quantum-resistant algorithms in embedded hardware and software will gain a substantial competitive advantage, driving a new wave of innovation and investment in future-proof security architectures for a vast array of critical devices.
| Opportunities | (~) Impact on CAGR % Forecast | Regional/Country Relevance | Impact Time Period |
|---|---|---|---|
| Growing Adoption of Edge Computing and AI at the Edge | +2.5% | Global | Mid-term (2027-2033) |
| Expansion of 5G Networks and Related IoT Devices | +2.0% | North America, Asia Pacific (China, South Korea), Europe | Mid-term (2027-2033) |
| Emergence of Post-Quantum Cryptography (PQC) | +1.8% | Global | Long-term (2030-2033) |
| Increased Demand for Cloud-Edge Security Integration | +1.5% | Global | Mid-term (2027-2033) |
| Vertical-Specific Security Solutions (e.g., Healthcare, Smart Cities) | +1.3% | North America, Europe, Asia Pacific | Short-term (2025-2028), Mid-term (2029-2033) |
Embedded Security Market Challenges Impact Analysis
The Embedded Security Market, while promising, faces several formidable challenges that require innovative solutions and strategic foresight. One significant challenge is the ever-evolving and increasingly sophisticated threat landscape. Attackers are constantly developing new techniques, including advanced persistent threats (APTs), supply chain attacks, and side-channel attacks, which are specifically designed to exploit vulnerabilities in embedded systems. This dynamic threat environment demands continuous updates, robust incident response capabilities, and a proactive security posture, which can be difficult to maintain for devices deployed in the field for extended periods, particularly those with limited connectivity or update mechanisms.
Another critical challenge lies in managing the secure lifecycle of embedded devices, from design and manufacturing to deployment, operation, and eventual decommissioning. Ensuring security across this entire lifecycle, including secure manufacturing processes, authenticated firmware updates, and robust key management, presents significant logistical and technical hurdles. Vulnerabilities introduced at any stage can compromise the entire system, and the difficulty of patching or replacing devices in remote or inaccessible locations further exacerbates this challenge, potentially leading to widespread security compromises.
Furthermore, the fragmentation of the embedded systems market, characterized by a vast array of hardware platforms, operating systems, and communication protocols, complicates the development and deployment of universal security solutions. This lack of uniformity makes it challenging to establish consistent security standards and best practices, leading to a fragmented security ecosystem where interoperability and comprehensive protection are difficult to achieve. Addressing this fragmentation requires industry-wide collaboration and the development of more adaptable and standardized security architectures to ensure broad applicability and effectiveness.
| Challenges | (~) Impact on CAGR % Forecast | Regional/Country Relevance | Impact Time Period |
|---|---|---|---|
| Evolving and Sophisticated Cyber Threat Landscape | -1.8% | Global | Short-term (2025-2028), Mid-term (2029-2033) |
| Managing Secure Lifecycle of Devices (Design to Decommission) | -1.4% | Global | Mid-term (2027-2033) |
| Fragmentation of Embedded Ecosystems and Standards | -1.0% | Global | Short-term (2025-2028) |
| Supply Chain Vulnerabilities and Trust Issues | -0.9% | Global | Short-term (2025-2028) |
| Compliance with Diverse and Evolving Regulations | -0.8% | Europe, North America, Asia Pacific | Short-term (2025-2028) |
Embedded Security Market - Updated Report Scope
This comprehensive market research report provides an in-depth analysis of the Embedded Security Market, covering historical data, current market trends, and future growth projections. It offers strategic insights into market dynamics, including drivers, restraints, opportunities, and challenges, providing a holistic view of the industry landscape. The report segments the market by component, type, application, deployment, and security level, offering detailed breakdowns and forecasts for each category across major global regions to facilitate informed decision-making for stakeholders.
| Report Attributes | Report Details |
|---|---|
| Base Year | 2024 |
| Historical Year | 2019 to 2023 |
| Forecast Year | 2025 - 2033 |
| Market Size in 2025 | USD 10.0 Billion |
| Market Forecast in 2033 | USD 26.0 Billion |
| Growth Rate | 12.5% |
| Number of Pages | 250 |
| Key Trends |
|
| Segments Covered |
|
| Key Companies Covered | Infineon Technologies AG, NXP Semiconductors N.V., STMicroelectronics N.V., Arm Holdings Plc, Microchip Technology Inc., Renesas Electronics Corporation, Qualcomm Incorporated, Intel Corporation, Thales Group, Rambus Inc., Broadcom Inc., Cisco Systems, Inc., IBM Corporation, Microsoft Corporation, Texas Instruments Incorporated, Samsung Electronics Co., Ltd., Synopsys Inc., Analog Devices, Inc., Green Hills Software, Inc., Irdeto. |
| Regions Covered | North America, Europe, Asia Pacific (APAC), Latin America, Middle East, and Africa (MEA) |
| Speak to Analyst | Avail customised purchase options to meet your exact research needs. Request For Analyst Or Customization |
Segmentation Analysis
The Embedded Security Market is intricately segmented across various dimensions to provide a granular understanding of its dynamics and growth trajectories. These segmentations enable stakeholders to identify niche opportunities and tailor strategies for specific market requirements. By component, the market is broadly divided into hardware, software, and services, reflecting the holistic approach required for embedded system protection. Hardware components, such as Secure Elements and TPMs, form the foundational trust anchors, while software provides the layers of defense for firmware, operating systems, and applications, supported by essential services like consulting and maintenance.
Further segmentation by type clarifies the specific security functions within embedded systems, ranging from fundamental authentication and encryption to advanced attack detection and secure boot mechanisms. This level of detail highlights the evolving landscape of threats and the corresponding need for specialized security capabilities. Application-wise, the market spans critical industry verticals including automotive, industrial IoT, consumer electronics, and healthcare, each presenting unique security challenges and regulatory environments that drive distinct demands for embedded security solutions.
Finally, the market is also analyzed by deployment models (cloud, on-premise, hybrid) and security levels (chip-level, device-level, network-level, cloud-level), showcasing how embedded security integrates into broader IT infrastructure and protects devices at different points of vulnerability. This comprehensive segmentation framework ensures that all facets of the market are covered, providing a detailed map for strategic planning and investment in the dynamic embedded security landscape.
- By Component:
- Hardware: Secure Element, Trusted Platform Module (TPM), Hardware Security Module (HSM), System-on-Chip (SoC) Security
- Software: Firmware Security, Operating System Security, Application Security
- Services: Consulting, Implementation, Support & Maintenance
- By Type:
- Authentication & Access Control
- Encryption & Data Protection
- Device Identity & Management
- Attack Detection & Prevention
- Secure Boot
- Firmware Over-The-Air (FOTA) Updates
- By Application/Industry Vertical:
- Automotive: Infotainment, ADAS, Telematics, V2X Communication
- Industrial: Industrial Control Systems (ICS), SCADA, IoT Devices
- Consumer Electronics: Smartphones, Wearables, Smart Home Devices
- Healthcare: Medical Devices, Patient Monitoring Systems
- Aerospace & Defense: Avionics, Drones, Communication Systems
- BFSI: Payment Terminals, ATMs
- Retail & Logistics
- Telecom
- By Deployment:
- Cloud
- On-Premise
- Hybrid
- By Security Level:
- Chip-level
- Device-level
- Network-level
- Cloud-level
Regional Highlights
- North America: This region is a dominant force in the Embedded Security Market, driven by the early adoption of advanced technologies, a strong presence of key market players, and significant investments in IoT, automotive, and industrial automation. Strict regulatory frameworks, particularly in critical infrastructure and data privacy, further bolster demand for robust embedded security solutions. The United States and Canada are at the forefront of innovation and implementation.
- Europe: Europe represents a mature market for embedded security, characterized by stringent data protection regulations like GDPR and a strong focus on industrial automation (Industry 4.0) and connected vehicles. Countries like Germany, the UK, and France are leading the adoption of embedded security in manufacturing, automotive, and smart city initiatives, emphasizing compliance and secure industrial control systems.
- Asia Pacific (APAC): APAC is projected to exhibit the highest growth rate due to rapid industrialization, massive investments in IoT infrastructure, and the burgeoning consumer electronics and automotive manufacturing sectors in countries like China, India, Japan, and South Korea. Increasing awareness of cyber threats and evolving local regulations are accelerating the demand for embedded security, making it a lucrative market.
- Latin America: This region is an emerging market for embedded security, with increasing digitalization across industries and a growing awareness of cybersecurity risks. While currently smaller in scale, the rising adoption of smart devices, industrial IoT, and digital transformation initiatives in countries like Brazil and Mexico present significant growth opportunities for embedded security solutions.
- Middle East and Africa (MEA): The MEA region is witnessing steady growth in embedded security, primarily fueled by government initiatives for smart city development, diversification of economies away from oil, and investments in critical infrastructure. The increasing deployment of IoT devices in sectors such as energy, healthcare, and smart buildings in countries like UAE, Saudi Arabia, and South Africa is driving the demand for embedded security.
Top Key Players
The market research report includes a detailed profile of leading stakeholders in the Embedded Security Market.- Infineon Technologies AG
- NXP Semiconductors N.V.
- STMicroelectronics N.V.
- Arm Holdings Plc
- Microchip Technology Inc.
- Renesas Electronics Corporation
- Qualcomm Incorporated
- Intel Corporation
- Thales Group
- Rambus Inc.
- Broadcom Inc.
- Cisco Systems, Inc.
- IBM Corporation
- Microsoft Corporation
- Texas Instruments Incorporated
- Samsung Electronics Co., Ltd.
- Synopsys Inc.
- Analog Devices, Inc.
- Green Hills Software, Inc.
- Irdeto
Frequently Asked Questions
What is embedded security?
Embedded security refers to the process of protecting embedded systems from cyber threats throughout their entire lifecycle. This involves integrating hardware-based and software-based security features directly into the device to ensure its integrity, confidentiality, and availability. It encompasses secure boot, secure storage, encryption, authentication, and firmware updates to prevent unauthorized access, tampering, and data breaches in purpose-built computing systems.
Why is embedded security important for IoT devices?
Embedded security is crucial for IoT devices because these devices are often resource-constrained, widely distributed, and handle sensitive data, making them vulnerable targets for cyberattacks. Robust embedded security protects IoT devices from unauthorized access, data manipulation, and malware infections, safeguarding user privacy, maintaining operational integrity, and preventing devices from being used as entry points for larger network attacks. It's essential for trust and reliability in the vast IoT ecosystem.
How does AI impact embedded security?
AI impacts embedded security by enhancing threat detection through anomaly analysis, predicting vulnerabilities, and enabling more adaptive defense mechanisms in real time, even on resource-limited devices. However, AI also introduces new security challenges, such as the potential for adversarial attacks on AI models and the need to secure the AI supply chain. Ultimately, AI serves as both a powerful tool for bolstering embedded security and a new attack surface requiring specialized protection.
What are the key challenges in implementing embedded security?
Key challenges in implementing embedded security include the resource constraints of many devices (limited processing, memory, power), the high cost and complexity of integrating advanced security features, the fragmented nature of embedded ecosystems with diverse hardware and software, and the ongoing need to manage secure device lifecycles from design to end-of-life. Additionally, the rapidly evolving cyber threat landscape demands continuous adaptation, complicating long-term security maintenance.
What are the future trends in embedded security?
Future trends in embedded security include a greater emphasis on hardware-rooted security and trusted execution environments, the widespread adoption of AI and machine learning for proactive threat intelligence and defense at the edge, the integration of post-quantum cryptography (PQC) to future-proof systems against quantum attacks, and a deeper focus on supply chain security to ensure component integrity. The convergence of IT and OT security and increasing regulatory mandates will also continue to shape the market.

