Hardware Encryption Market
Hardware Encryption Market Size, Scope, Growth, Trends and By Segmentation Types, Applications, Regional Analysis and Industry Forecast (2025-2033)
Report ID : RI_705545 | Last Updated : August 17, 2025 |
Format : ![]()
![]()
![]()
![]()
Hardware Encryption Market Size
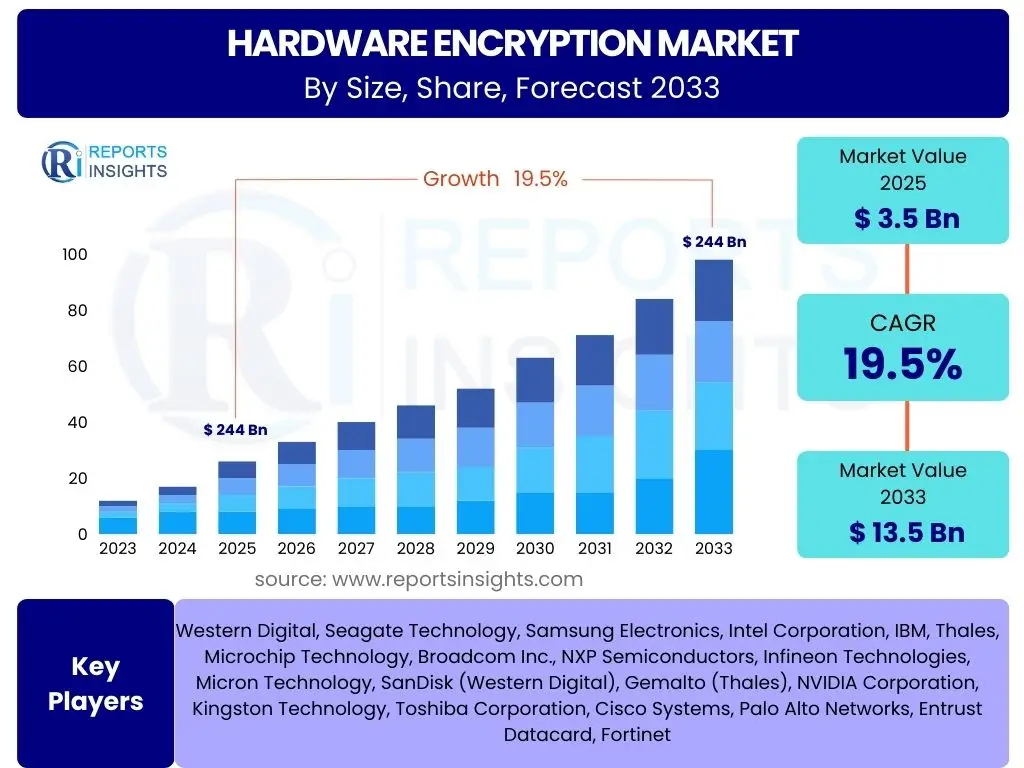
According to Reports Insights Consulting Pvt Ltd, The Hardware Encryption Market is projected to grow at a Compound Annual Growth Rate (CAGR) of 19.5% between 2025 and 2033. The market is estimated at USD 3.5 Billion in 2025 and is projected to reach USD 13.5 Billion by the end of the forecast period in 2033.
Key Hardware Encryption Market Trends & Insights
The Hardware Encryption Market is experiencing dynamic shifts driven by escalating cybersecurity threats, stringent regulatory compliance, and the pervasive adoption of cloud computing and IoT devices. Users are increasingly concerned about data breaches and the need for robust, foundational security at the hardware level. This includes a growing interest in self-encrypting drives (SEDs), hardware security modules (HSMs), and secure enclaves within processors, recognizing the inherent vulnerabilities of software-only encryption. The market reflects a clear demand for integrated, high-performance security solutions that do not compromise system efficiency.
Furthermore, the convergence of operational technology (OT) and information technology (IT) environments, coupled with the expansion of edge computing, is creating new frontiers for hardware encryption. Organizations are seeking solutions that can protect sensitive data in transit and at rest across diverse and distributed infrastructures. The focus is also shifting towards supply chain security, with a desire for transparent and verifiable hardware components to mitigate risks from pre-installed vulnerabilities or malicious tampering. This comprehensive approach underscores the market's evolution towards more resilient and tamper-proof security paradigms.
- Increasing adoption of self-encrypting drives (SEDs) for data at rest.
- Rising demand for Hardware Security Modules (HSMs) in critical infrastructure and cloud environments.
- Integration of encryption capabilities at the processor level (e.g., Intel SGX, AMD SEV).
- Growing emphasis on secure boot and trusted execution environments (TEEs).
- Expansion of hardware encryption into IoT and automotive sectors for device and data integrity.
- Evolving regulatory landscape (GDPR, CCPA, HIPAA) driving compliance with strong encryption.
- Shift towards quantum-resistant cryptographic algorithms in hardware.
- Focus on supply chain security and verified hardware components.
AI Impact Analysis on Hardware Encryption
User inquiries concerning AI's impact on hardware encryption frequently revolve around potential threats, such as AI-powered cryptanalysis or sophisticated side-channel attacks, and opportunities for enhanced security, including AI-driven anomaly detection and intelligent key management. There is a clear anticipation that AI could both fortify and challenge existing cryptographic paradigms. The primary concern is whether AI could accelerate the cracking of current encryption standards, necessitating more resilient hardware-based solutions, particularly in the face of quantum computing advancements. Conversely, users also envision AI as a tool to automate and optimize security processes, making hardware encryption more adaptive and less prone to human error.
The integration of AI into hardware encryption is expected to manifest in several ways, from optimizing cryptographic operations to bolstering defenses against novel attack vectors. AI algorithms can analyze vast datasets to identify unusual access patterns or potential compromises, enhancing the proactive security posture of hardware devices. Furthermore, AI could play a role in the lifecycle management of encryption keys, improving their generation, storage, and revocation. While the potential for AI to be misused in offensive cybersecurity is acknowledged, the prevailing sentiment is that its application in defensive mechanisms, especially in hardware-enforced security, offers significant advantages for future data protection.
- AI-powered anomaly detection enhancing threat intelligence for hardware security.
- Optimization of cryptographic operations and key management through machine learning algorithms.
- Potential for AI to accelerate development of post-quantum cryptographic hardware.
- Increased complexity and sophistication of AI-driven side-channel attacks on hardware.
- AI-enhanced firmware analysis for detecting vulnerabilities in hardware encryption implementations.
- Automated incident response and real-time threat mitigation for hardware-level breaches.
Key Takeaways Hardware Encryption Market Size & Forecast
The Hardware Encryption Market is poised for substantial expansion, reflecting a global imperative for advanced data security solutions in an increasingly interconnected and threat-laden digital landscape. Key takeaways from the market's size and forecast underscore a robust growth trajectory, primarily fueled by the unrelenting surge in cyberattacks, the proliferation of data-intensive technologies like IoT and cloud services, and the tightening grip of data privacy regulations worldwide. Businesses and governments alike are recognizing that foundational security, rooted in hardware, is indispensable for protecting sensitive information from the earliest points of interaction.
The forecast indicates a sustained shift towards integrated hardware security, moving beyond traditional software-only approaches due to their inherent limitations. This growth is not merely volumetric but also qualitative, driven by innovations in cryptographic algorithms, secure processing technologies, and the embedding of security features directly into devices and infrastructure. Stakeholders should prioritize investments in high-performance, tamper-resistant hardware encryption solutions that offer both compliance and resilience, ensuring that data integrity and confidentiality are maintained across diverse operating environments and emerging technological frontiers.
- Significant market growth driven by increasing data breaches and cyber threats.
- Strong adoption of hardware encryption solutions across various industries for enhanced data protection.
- Regulatory compliance (e.g., GDPR, CCPA) serving as a major catalyst for market expansion.
- Technological advancements in processor-level encryption and secure element integration.
- Cloud and IoT proliferation necessitating robust hardware-based security for distributed systems.
- Emergence of quantum computing creating demand for future-proof, quantum-resistant hardware encryption.
Hardware Encryption Market Drivers Analysis
The Hardware Encryption Market is propelled by a confluence of critical factors, primarily the escalating frequency and sophistication of cyberattacks, which necessitate more robust and immutable security layers. Data breaches and ransomware incidents have underscored the inadequacy of software-only defenses, driving organizations towards hardware-enforced security as a more resilient alternative. Furthermore, the global proliferation of stringent data privacy regulations, such as GDPR and CCPA, mandates enhanced data protection measures, making hardware encryption a compliance imperative for businesses handling sensitive information. The inherent tamper-resistance and performance advantages of hardware over software encryption are increasingly recognized as essential for maintaining data integrity and confidentiality across diverse operational environments.
Another significant driver is the rapid expansion of cloud computing and the Internet of Things (IoT). As more data is stored, processed, and transmitted in cloud environments and by myriad interconnected devices, the demand for embedded, high-performance encryption at the source becomes paramount. Hardware encryption ensures data security at rest, in transit, and in use, providing a foundational layer of trust from the endpoint to the cloud. This trend is further amplified by the growing adoption of digital transformation initiatives across industries, necessitating secure infrastructure to support advanced analytics, artificial intelligence, and remote work models, all of which rely heavily on secure data handling.
| Drivers | (~) Impact on CAGR % Forecast | Regional/Country Relevance | Impact Time Period |
|---|---|---|---|
| Increasing Sophistication of Cyber Threats and Data Breaches | +5.2% | Global, particularly North America, Europe, APAC | Short-term to Long-term (2025-2033) |
| Strict Regulatory Compliance and Data Privacy Laws (e.g., GDPR, CCPA) | +4.8% | Europe, North America, parts of Asia | Mid-term (2025-2030) |
| Proliferation of Cloud Computing and IoT Devices | +4.5% | Global, especially tech hubs and developing economies | Short-term to Long-term (2025-2033) |
| Growing Demand for Secure Storage Solutions (e.g., SEDs, HSMs) | +3.9% | Global, across BFSI, Government, Healthcare | Mid-term (2025-2030) |
| Performance Advantages and Tamper-Resistance of Hardware Encryption | +3.5% | Global, industries requiring high-speed processing | Long-term (2028-2033) |
Hardware Encryption Market Restraints Analysis
Despite its significant advantages, the Hardware Encryption Market faces several notable restraints that could impede its growth. One primary challenge is the higher initial cost associated with hardware-based encryption solutions compared to software-only alternatives. This cost factor can be a barrier for small and medium-sized enterprises (SMEs) or organizations with limited IT budgets, who may opt for less secure but more affordable software solutions. Additionally, the complexity involved in integrating hardware encryption into existing IT infrastructures, especially legacy systems, can pose significant challenges, requiring specialized expertise and potentially leading to downtime during implementation.
Another restraint stems from the lack of widespread standardization and interoperability across different hardware encryption vendors and technologies. This fragmentation can lead to vendor lock-in and complicate the management of diverse encryption solutions within a single enterprise. Furthermore, the perceived performance overhead, though often negligible for modern hardware encryption, can sometimes be a concern for highly sensitive applications where even minimal latency is unacceptable. Addressing these technical and economic barriers through increased standardization, ease of integration, and greater awareness of long-term benefits will be crucial for overcoming these market restraints.
| Restraints | (~) Impact on CAGR % Forecast | Regional/Country Relevance | Impact Time Period |
|---|---|---|---|
| High Initial Cost of Hardware Encryption Solutions | -3.1% | Global, particularly SMEs in developing regions | Short-term to Mid-term (2025-2029) |
| Complexity of Integration with Existing Infrastructure | -2.8% | Global, especially organizations with legacy systems | Mid-term (2026-2030) |
| Lack of Standardization and Interoperability | -2.5% | Global, impacting large enterprises with diverse IT | Long-term (2028-2033) |
| Perceived Performance Overhead and Latency Concerns | -2.0% | Global, for high-performance computing environments | Short-term (2025-2027) |
| Limited Awareness and Expertise Among End-Users | -1.5% | Developing economies, non-tech industries | Short-term to Mid-term (2025-2029) |
Hardware Encryption Market Opportunities Analysis
The Hardware Encryption Market is rich with untapped opportunities driven by emerging technological paradigms and evolving security requirements. The advent of quantum computing, while a potential threat to current cryptographic methods, simultaneously presents a significant opportunity for the development and deployment of quantum-resistant hardware encryption. Organizations are proactively seeking solutions that can future-proof their data against the anticipated capabilities of quantum machines, creating a new niche for specialized hardware capable of executing post-quantum algorithms. This represents a substantial area for research, development, and commercialization, pushing the boundaries of cryptographic engineering.
Beyond quantum computing, the rapid expansion of the automotive industry, particularly in autonomous vehicles and connected cars, offers a vast new frontier for hardware encryption. Securing vehicle communication, firmware, and sensor data is critical for safety and privacy, making embedded hardware encryption a vital component. Similarly, the integration of blockchain technology into various industries, from supply chain management to financial services, presents opportunities for hardware-based trusted execution environments and cryptographic accelerators to enhance the security and integrity of distributed ledgers. These emerging applications, coupled with the increasing emphasis on supply chain security for hardware components, open up diverse avenues for market expansion and innovation.
| Opportunities | (~) Impact on CAGR % Forecast | Regional/Country Relevance | Impact Time Period |
|---|---|---|---|
| Development of Quantum-Resistant Hardware Encryption | +4.5% | Global, particularly advanced tech economies | Mid-term to Long-term (2028-2033) |
| Expansion into Automotive and Industrial IoT (IIoT) Security | +4.2% | North America, Europe, Asia Pacific (China, Japan) | Mid-term (2026-2031) |
| Integration with Blockchain Technology and Distributed Ledgers | +3.8% | Global, especially BFSI, Supply Chain, Healthcare | Mid-term to Long-term (2027-2033) |
| Increasing Demand for Supply Chain Security of Hardware Components | +3.5% | Global, high-security sectors (Government, Defense) | Short-term to Mid-term (2025-2030) |
| Growth in Edge Computing and Fog Computing Deployments | +3.0% | Global, especially smart cities, remote monitoring | Short-term (2025-2028) |
Hardware Encryption Market Challenges Impact Analysis
The Hardware Encryption Market, while promising, faces several inherent challenges that demand strategic responses from industry players. One significant challenge is the ongoing evolution of the threat landscape, where sophisticated adversaries continuously develop new methods to bypass security measures, including side-channel attacks targeting hardware implementations. This necessitates constant innovation and updates to hardware designs and cryptographic algorithms, which can be costly and complex. Moreover, the global shortage of skilled cybersecurity professionals and engineers proficient in hardware-level security poses a significant hurdle for both developing and deploying advanced encryption solutions, limiting adoption and effective management.
Another critical challenge revolves around the transition to post-quantum cryptography. While an opportunity, it also represents a substantial technical and logistical challenge to migrate existing infrastructure and devices to new, quantum-resistant algorithms without disrupting operations. This transition requires significant investment in research and development, as well as coordinated efforts across the industry. Furthermore, ensuring the integrity and trustworthiness of the hardware supply chain is a persistent concern, as malicious implants or backdoors introduced during manufacturing could compromise the entire security posture, undermining the very purpose of hardware encryption.
| Challenges | (~) Impact on CAGR % Forecast | Regional/Country Relevance | Impact Time Period |
|---|---|---|---|
| Evolving Threat Landscape and Sophisticated Attack Vectors (e.g., Side-channel) | -3.5% | Global | Short-term to Long-term (2025-2033) |
| Shortage of Skilled Cybersecurity Professionals in Hardware Security | -3.0% | Global, particularly developed economies | Mid-term (2026-2031) |
| Complex and Costly Transition to Post-Quantum Cryptography | -2.8% | Global, high-security and critical infrastructure sectors | Long-term (2029-2033) |
| Ensuring Supply Chain Security and Trustworthiness of Hardware | -2.5% | Global, particularly manufacturing hubs and sensitive regions | Short-term to Mid-term (2025-2030) |
| Interoperability Issues and Ecosystem Fragmentation | -2.0% | Global | Mid-term (2026-2030) |
Hardware Encryption Market - Updated Report Scope
This comprehensive report provides an in-depth analysis of the global Hardware Encryption Market, offering valuable insights into its current landscape, future projections, and the underlying dynamics shaping its growth. It covers a detailed assessment of market size, trends, drivers, restraints, opportunities, and challenges across various segments and key geographical regions. The report aims to equip stakeholders with a thorough understanding of market intricacies, enabling informed strategic decision-making and competitive positioning within this critical cybersecurity domain.
| Report Attributes | Report Details |
|---|---|
| Base Year | 2024 |
| Historical Year | 2019 to 2023 |
| Forecast Year | 2025 - 2033 |
| Market Size in 2025 | USD 3.5 Billion |
| Market Forecast in 2033 | USD 13.5 Billion |
| Growth Rate | 19.5% |
| Number of Pages | 247 |
| Key Trends |
|
| Segments Covered |
|
| Key Companies Covered | Western Digital, Seagate Technology, Samsung Electronics, Intel Corporation, IBM, Thales, Microchip Technology, Broadcom Inc., NXP Semiconductors, Infineon Technologies, Micron Technology, SanDisk (Western Digital), Gemalto (Thales), NVIDIA Corporation, Kingston Technology, Toshiba Corporation, Cisco Systems, Palo Alto Networks, Entrust Datacard, Fortinet |
| Regions Covered | North America, Europe, Asia Pacific (APAC), Latin America, Middle East, and Africa (MEA) |
| Speak to Analyst | Avail customised purchase options to meet your exact research needs. Request For Analyst Or Customization |
Segmentation Analysis
The Hardware Encryption Market is comprehensively segmented across several dimensions, including Type, Standard, End-User Industry, and Application, each offering unique insights into market dynamics and growth opportunities. This granular segmentation allows for a detailed analysis of specific product categories, compliance requirements, industry-specific adoption patterns, and the diverse use cases that drive demand for hardware-based security solutions. Understanding these segments is crucial for identifying niche markets, tailoring product development, and devising targeted marketing strategies to address the varied needs of different market participants.
- By Type: This segment includes various forms of hardware incorporating encryption, such as USB Devices (encrypted flash drives), Internal Hard Drives (HDD/SSD with built-in encryption), External Hard Drives, Solid State Drives (SSDs), Network Attached Storage (NAS) devices, Servers equipped with encryption capabilities, and Other specialized hardware like Hardware Security Modules (HSMs), Trusted Platform Modules (TPMs), and Field-Programmable Gate Arrays (FPGAs) designed for cryptographic acceleration.
- By Standard: This segment differentiates the market based on the cryptographic standards and certifications met by the hardware. Key standards include FIPS (Federal Information Processing Standards) 140-2/3, a U.S. government computer security standard used to accredit cryptographic modules, and Common Criteria (ISO/IEC 15408), an international standard for computer security certification. Other standards like TCG (Trusted Computing Group) and IEEE 1667 also play a role in ensuring interoperability and security.
- By End-User Industry: This segmentation highlights the primary sectors adopting hardware encryption solutions. Major industries include Banking, Financial Services, and Insurance (BFSI) for secure transactions and data storage; Government & Public Sector for classified information; IT & Telecom for protecting vast networks and cloud infrastructure; Healthcare for patient data privacy (HIPAA compliance); Retail & E-commerce for payment security; Manufacturing for intellectual property protection; Aerospace & Defense for national security; Automotive for connected car security; and Energy & Utilities for critical infrastructure protection.
- By Application: This segment categorizes hardware encryption based on its primary use cases. These include general Data Protection for securing data at rest and in transit; Network Security for protecting communications channels; Cloud Security for securing data and applications in cloud environments; IoT Security for device and data integrity in interconnected systems; Payment Security for securing financial transactions; and Critical Infrastructure Protection for safeguarding essential services from cyber threats.
Regional Highlights
- North America: This region holds a significant share in the Hardware Encryption Market, driven by stringent regulatory frameworks (e.g., HIPAA, GLBA, CCPA), a high concentration of tech companies, and a strong focus on cybersecurity investments across BFSI, government, and IT sectors. The early adoption of advanced technologies and the presence of major market players contribute to its dominance.
- Europe: Europe is a key market propelled by the pervasive influence of GDPR and NIS Directive, mandating robust data protection and cybersecurity measures. Countries like Germany, the UK, and France are leading in adopting hardware encryption, particularly in financial services, government, and healthcare, due to increasing cyber threats and a mature regulatory landscape.
- Asia Pacific (APAC): APAC is projected to exhibit the highest growth rate, fueled by rapid digital transformation, increasing internet penetration, and a burgeoning smart cities movement. Countries like China, India, Japan, and South Korea are experiencing significant investments in cloud infrastructure, IoT, and industrial automation, leading to a surge in demand for hardware security solutions, despite nascent regulatory environments in some areas.
- Latin America: This region is experiencing steady growth in hardware encryption adoption, primarily driven by increasing awareness of cybersecurity risks and developing data protection laws. Brazil and Mexico are leading the charge, with demand emerging from financial institutions and telecommunications sectors seeking to secure critical data and infrastructure.
- Middle East and Africa (MEA): The MEA region is witnessing gradual adoption, primarily influenced by growing digitalization initiatives in the Gulf Cooperation Council (GCC) countries and increasing foreign investments. Emphasis on critical infrastructure protection and smart city projects, particularly in countries like UAE and Saudi Arabia, is fostering the demand for advanced hardware security solutions.
Top Key Players
The market research report includes a detailed profile of leading stakeholders in the Hardware Encryption Market.- Western Digital Corporation
- Seagate Technology Holdings plc
- Samsung Electronics Co., Ltd.
- Intel Corporation
- International Business Machines Corporation (IBM)
- Thales Group
- Microchip Technology Inc.
- Broadcom Inc.
- NXP Semiconductors N.V.
- Infineon Technologies AG
- Micron Technology, Inc.
- Kingston Technology Company, Inc.
- Toshiba Corporation
- Cisco Systems, Inc.
- Palo Alto Networks, Inc.
- Entrust Corporation
- Fortinet, Inc.
- Analog Devices, Inc.
- SK Hynix Inc.
- Rambus Inc.
Frequently Asked Questions
Analyze common user questions about the Hardware Encryption market and generate a concise list of summarized FAQs reflecting key topics and concerns.What is Hardware Encryption?
Hardware encryption is a method of converting data into an unreadable format using a dedicated cryptographic processor or module embedded within a physical device, such as a hard drive, USB drive, or CPU. Unlike software encryption, it offers enhanced security, performance, and resistance to tampering, as the encryption keys are stored and managed within the hardware itself.
Why is Hardware Encryption important for data security?
Hardware encryption is crucial for data security because it provides a more robust and immutable layer of protection than software-only solutions. It is less vulnerable to malware and operating system attacks, offers superior performance, and ensures that data remains encrypted even if the device is lost, stolen, or accessed by unauthorized individuals, thereby protecting sensitive information at rest and in transit.
What are the primary drivers of the Hardware Encryption Market growth?
The primary drivers include the escalating frequency and sophistication of cyberattacks, stringent data privacy regulations (e.g., GDPR, CCPA), the widespread adoption of cloud computing and IoT devices, and the inherent performance and security advantages of hardware over software encryption. These factors compel organizations to invest in foundational, hardware-level security.
What types of devices commonly utilize Hardware Encryption?
Common devices utilizing hardware encryption include Self-Encrypting Drives (SEDs) like internal and external hard drives and SSDs, USB flash drives, Hardware Security Modules (HSMs) for cryptographic key management, and processors with built-in secure enclaves (e.g., Intel SGX, AMD SEV). It's also increasingly found in network devices and IoT endpoints.
How does Quantum Computing impact the future of Hardware Encryption?
Quantum computing poses a potential long-term threat to current cryptographic algorithms, necessitating the development of quantum-resistant hardware encryption. This drives a significant opportunity for research and investment in new cryptographic standards and hardware designs capable of withstanding quantum attacks, ensuring future data security.

